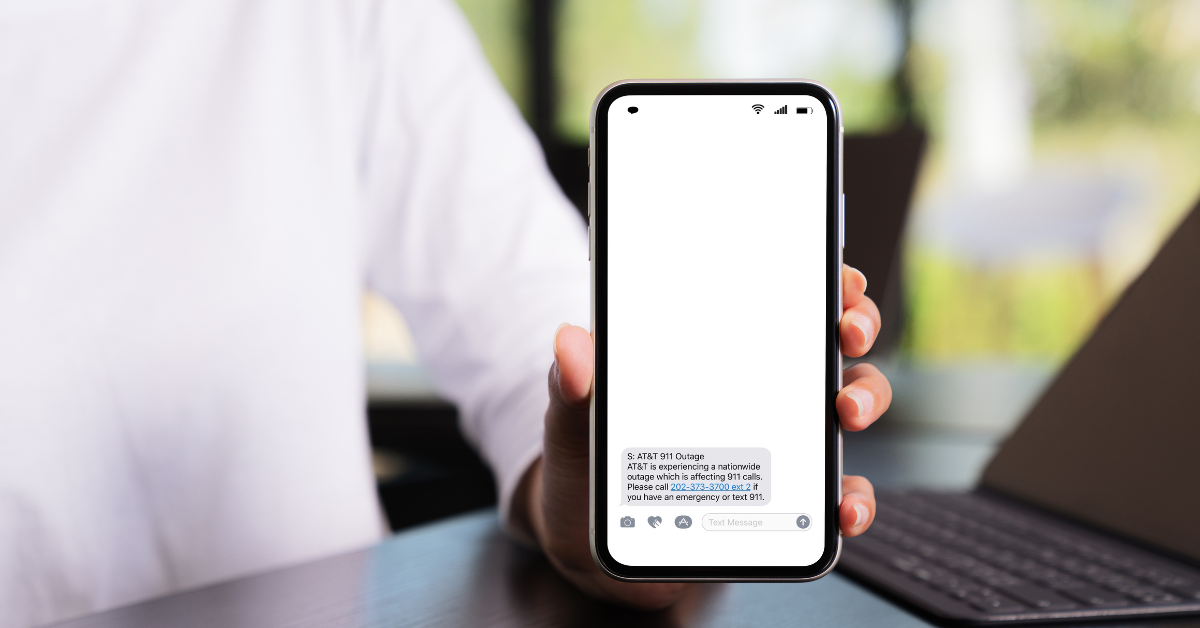
As our headline suggests, AT&T experienced a massive outage Feb. 22 which affected their cell network nationwide. The outage affected over 70,000 reported customers (the actual numbers are certainly much higher) and left many unable call, text or even reach 911 for 12 hours. Many police departments report seeing an increase in 911 calls as some customers tried dialing to see if the call would go through.
AT&T had been seeing an increase in outages affecting their networks ahead of the major outage that occurred last Thursday. The outage lasted just under 12 hours and it was enough time for speculation as to the cause to run rampant across the internet.
AT&T has confirmed the outage was not due to a cyber incident but instead a botched update that took their networks offline. They also confirmed no customer data was lost In the event. The outage hit consumers and business customers alike.
According to AT&T’s own landing page about the incident, consumers will be seeing a credit issued to their accounts automatically ($5.00 at the time of writing) and they say they will work with business customers individually to compensate for the down time.
For some customers that might feel like too little to compensate for the inconvenience caused and at least one state’s attorney general agrees, with New York Attorney General Letitia James announcing they’ll be conducting an investigation into the matter.
“Americans rely on cell service providers for consistent and reliable service to help them with nearly every aspect of their daily lives,” New York Attorney General Letitia James said. “Nationwide outages are not just an inconvenience, they can be dangerous, and it’s critical that we protect consumers when an outage occurs.”
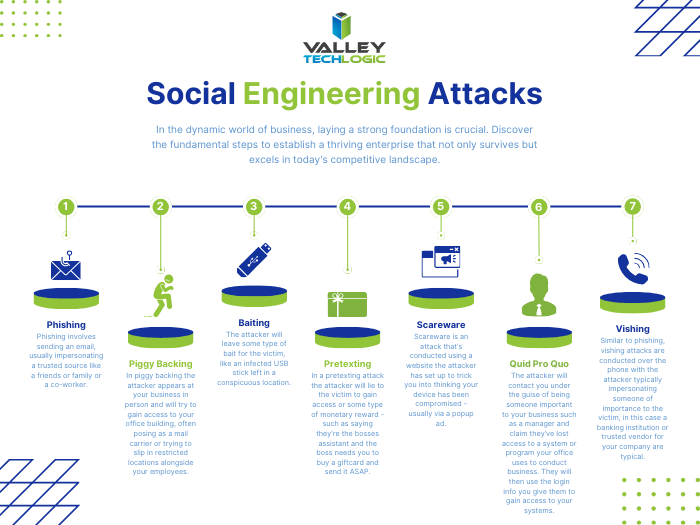
There are also some concerns surrounding the credit that’s going to be issued and whether scammers may take advantage of the situation for their own gain. Consumers should be extra vigilant when opening and responding to emails relating to credit or compensation from AT&T. At the time of writing AT&T has said consumers do not need to do anything on their end to receive the credit. We especially want to warn against clicking on any links with the promise of compensation, which is inadvisable well beyond the current situation.
Consumers should also avoid responding to text messages or phone calls requesting their information to receive the credit, again AT&T will not be contacting customers directly, and any communications should be directed at official lines of communication. If you’re not sure how to contact AT&T, we suggest referring to a recent bill.
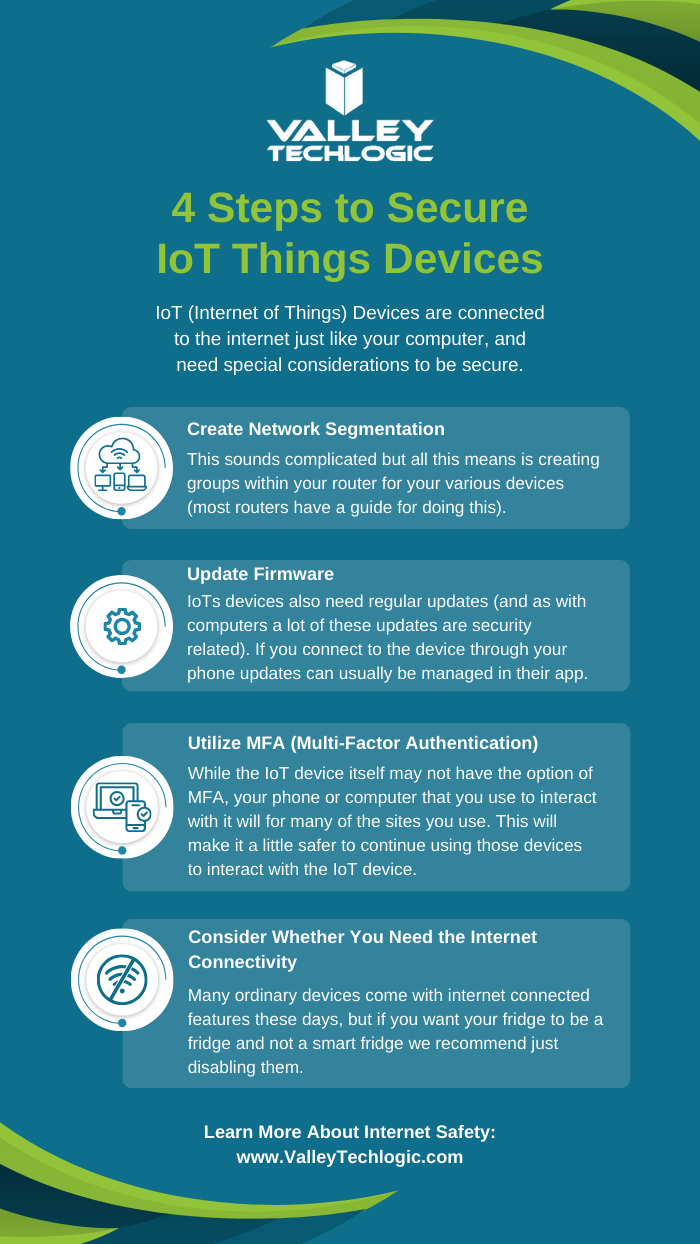
For businesses, downtime like this can be more than an inconvenience, it can affect your business in major ways and be financially very costly.
At Valley Techlogic, we have strategies to prevent outages from affecting your business or your bottom line and our clients rely on our expert advice for navigating technology solutions for their business. Reach out to us today to learn more.
 Looking for more to read? We suggest these other articles from our site.
Looking for more to read? We suggest these other articles from our site.
-
China sponsored hacking data dump highlights the importance of seeing the bigger picture when it comes to your cyber security protections
-
5 Reasons to have an annual meeting with your IT service provider and how to make the most of it
-
CMMC Changes for 2024 Summarized
-
Can outsourcing your IT save you time and money? 4 proven benefits to outsourcing your IT
This article was powered by Valley Techlogic, an IT service provider in Atwater, CA. You can find more information at https://www.valleytechlogic.com/ or on Facebook at https://www.facebook.com/valleytechlogic/ . Follow us on Twitter at https://x.com/valleytechlogic.