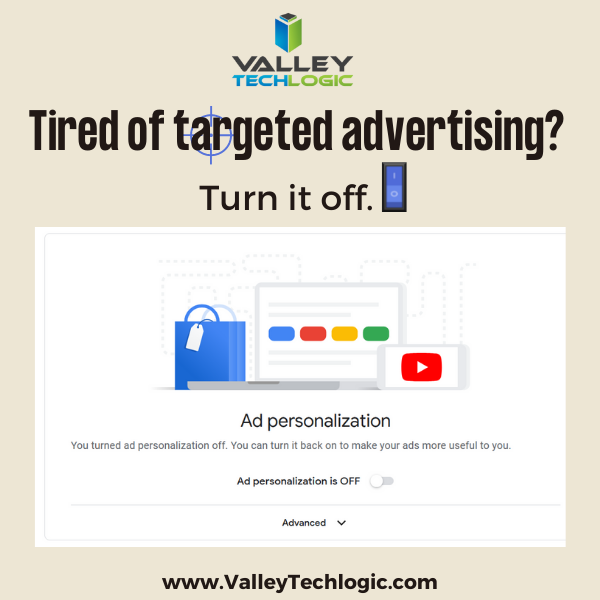
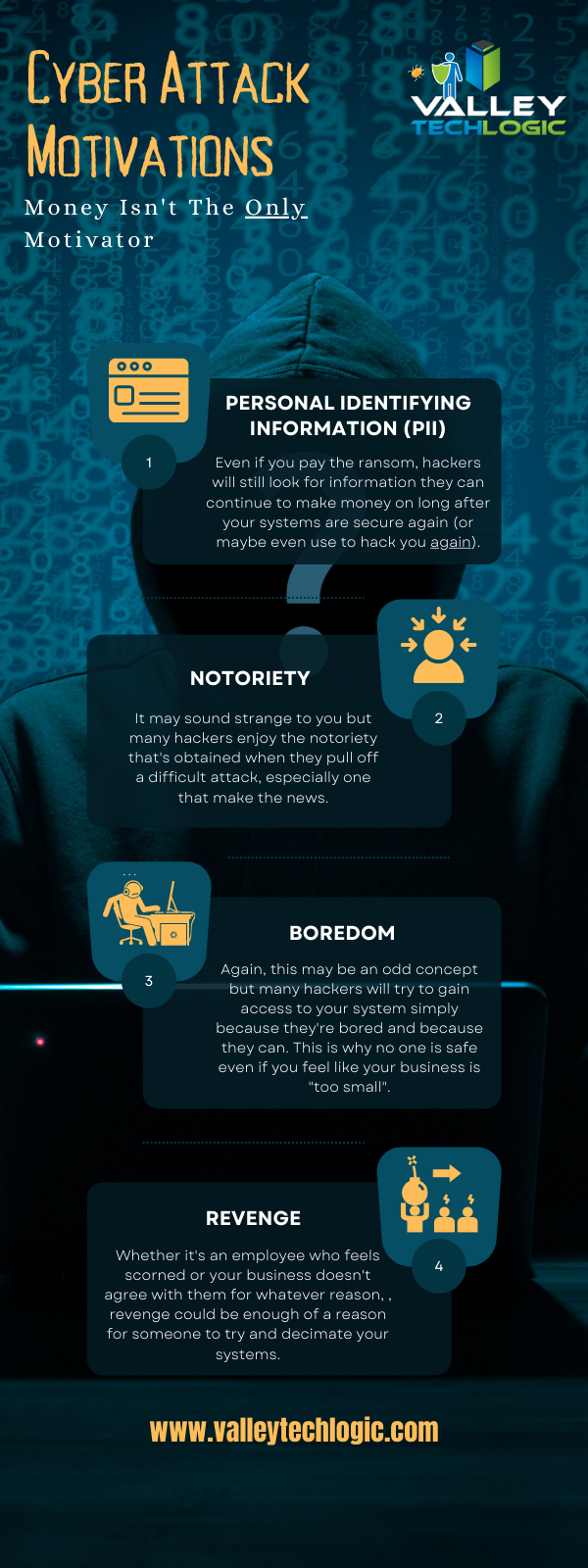
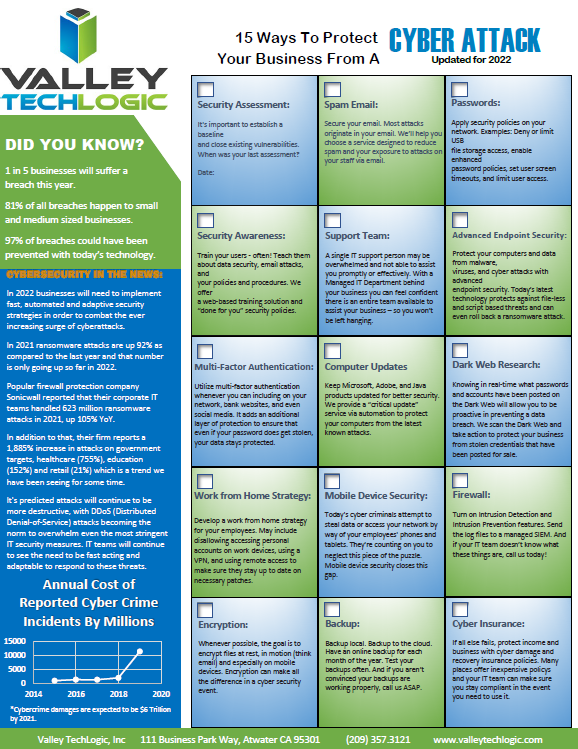
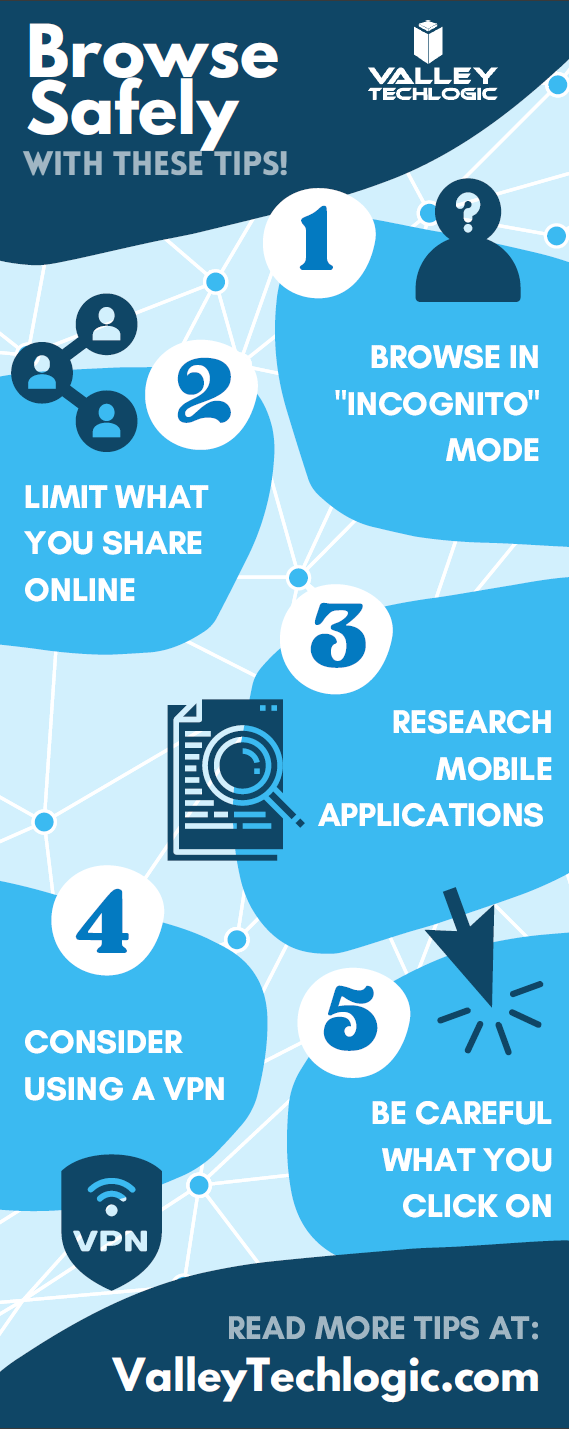
There’s an onslaught of information aimed at internet safety and most of it lets be honest, falls on deaf ears.
Most people online today feel like they’re technology savvy enough to avoid the scams out there (unfortunately at least 1 out of 6 are wrong) and even if you acknowledge tech falls outside your scope of expertise you’re still at risk.
The good news is we have a list of 10 things you can do today even if you’re technologically challenged that will make a major impact on the network safety in your office.
- Confirm your backups are working. Backups are one of your best defenses against ransomware, especially if you have an archival copy which is a backup copy that’s made once and then tucked away until you need it (usually behind layers of security, like with our TechVault solution).
- Security awareness training for you and your employees. When we know better, we do better. Many security awareness training programs are implemented in bite size doses that are easy to squeeze into your day. It’s easier to avoid a phishing scam if you’ve seen the obvious examples through training.
- Speaking of phishing scams, don’t open suspicious emails. We’ve talked a lot about this topic including how to spot a phishing email, but email scams are one of the top ways hackers can infiltrate your network.
- Upgrade software that’s reached End of Life (EoL). If your office computers are still on Windows 7 it’s definitely time for an upgrade and technically you can still upgrade to Windows 10 for free. While other upgrades may not be free, it’s still a good idea to get rid of software that’s no longer being supported by the vendor.
- You should also make sure all the software you need to stay safe online is installed on your devices. Programs can go missing or just not be reinstalled if a computer needs to be wiped for whatever reason, you should make sure important software such as anti-virus detection is installed on all of your office computers.
- While you’re at it, it’s time to serious think about Multi-Factor Authentication. We always hear a collective groan when this topic comes up, but password managers have become much easier to use and can even make logging into the various sites you use to work easier. Here are our top picks.
- Remove any devices you’re no longer using from your network. Besides being a waste of electricity, devices connected to your network that aren’t being used can be vessels for infiltration if they’re not being kept up to date via patching etc. Get rid of them!
- Have a plan for reporting suspicious activity. Do your employees know what to do if they receive a suspicious email or their computers acting “funny”? Having a plan documented somewhere (even if the only advice is “Contact our IT service team”) can mean a cyber threat event is recorded and dealt with instead of just ignored because they didn’t know what to do.
- Have an office password policy guide as well. It’s a good idea to have a guide for passwords available to your employees, especially if it covers what not to do such as having your phone number or any other PII (Personal Identifying Information) as your password.
- Know when to ask for help. This list is a good place to start but if your business has no IT help now (or possibly worse, inadequate help) it’s a good idea to call in the experts. Calling Valley Techlogic for a free consultation is another step you can take today to improve the safety of your office network.
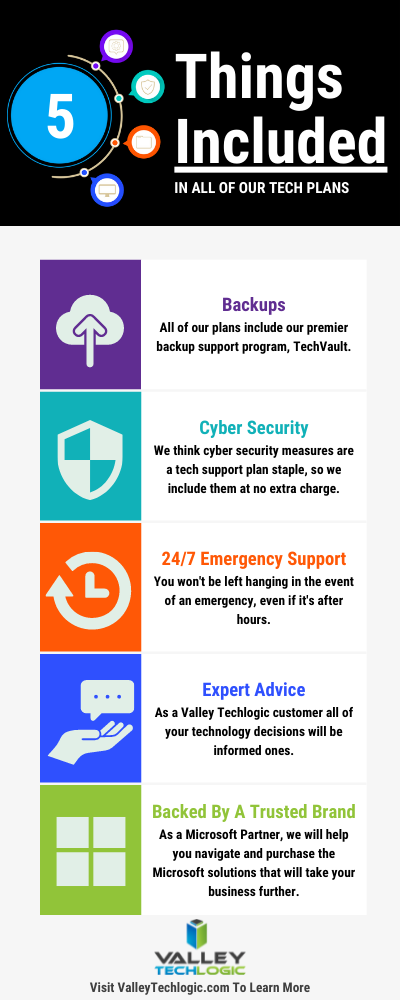
Here are 5 things all Valley Techlogic Plans includes:
Want to learn more? Reach out today for a free consultation and learn how Valley Techlogic can specifically support your business’s technology.
Looking for more to read? We suggest these other articles from our site.
-
Is it time to call in the reinforcements? 5 benefits to co-managed IT services
-
On average, your information is shared 747 times a day according to a new study
-
College shuttered after 157 years due to ransomware attack
-
Technology that you can build on, supporting your construction business through tech
This article was powered by Valley TechLogic, an IT service provider in Atwater, CA. You can find more information at https://www.valleytechlogic.com/ or on Facebook at https://www.facebook.com/valleytechlogic/ . Follow us on Twitter at https://x.com/valleytechlogic.