We find with our clients we find they’re often unaware they have a personal cloud storage solution right at their fingers tips and included for free with their Microsoft 365 subscription, OneDrive.
Every Microsoft 365 business subscription user will have 1 TB of storage space free with their Microsoft 365 subscription. If you have an IT provider managing your Microsoft 365 subscriptions they probably have set this up to backup certain folders by default, usually your documents, pictures and desktop folders.
These folders will automatically be synchronized to the cloud, so it provides excellent protection if one of your company devices is lost, stolen or breaks. It’s also a good cybersecurity measure to have your company workstations backed up in someway so if there’s ever a cybersecurity attack that effects your office, not all of your files will be lost.
On that note, Microsoft does operate on what they call a “shared responsibility” model, so if your Microsoft account is compromised as well you may still lose those files even if they were backed up (which is why we always recommend enabling 2-Factor Authentication, Microsoft makes it easy).
If OneDrive is successfully enabled on a device you’ll see a little blue cloud icon on your task bar, that when you hover over will tell you the status of your backup (it should say your files are up to date).
 Clicking on the blue cloud will allow you a glimpse at what files have been backed up recently, as well as a quick way to access the OneDrive folder located on your computer as well as the one that’s found online.
Clicking on the blue cloud will allow you a glimpse at what files have been backed up recently, as well as a quick way to access the OneDrive folder located on your computer as well as the one that’s found online.
1 Terabyte of storage is plenty for most users, but if you’re a heavy data user or someone in charge of most of the documentation for your office you may need more. Microsoft offers OneDrive plans outside of the 1 TB you receive for free as a Microsoft 365 user, see our chart below:
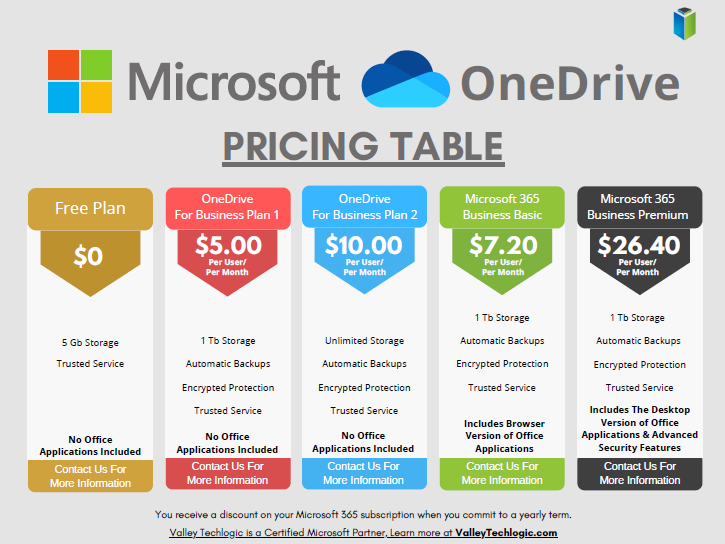 Also, if you just want to try the service out but you’re not yet a Microsoft 365 user, you can either purchase a OneDrive subscription outside of the Microsoft 365 service (though we wouldn’t necessarily recommend it, Microsoft 365 is a better value) or you can test drive the service with their completely free 5 gigabyte storage option.
Also, if you just want to try the service out but you’re not yet a Microsoft 365 user, you can either purchase a OneDrive subscription outside of the Microsoft 365 service (though we wouldn’t necessarily recommend it, Microsoft 365 is a better value) or you can test drive the service with their completely free 5 gigabyte storage option.
5 GB is not a lot of storage these days but if you’re wanting to see if the service would be a good fit for you, it’s plenty for a good test run.
Once you have your OneDrive set up, you might be thinking about how you’re going to organize it. Luckily, for the folders you back up any pre-existing folder organization you have will be backed up as well. If you have a sub-folder inside your Documents folder labeled “Mikes Important Files 8/20/2019” that same sub-folder will exist in your OneDrive.
Besides that, here are 5 fast and easy folder organization tips:
- Don’t let files languish in your Downloads folder. I’m guilty of this myself, you’re busy and files you receive from colleagues or make just never make it out of their origination folder. It’s a good habit as you go to organization your new OneDrive space to sort things as they come in.
- Organize things by project or by date. When you’re looking for work and documents around a certain task or event, sorting by the date or by project is a good system to easily find them again. I’m in favor of by project myself.
- Use descriptive names, there’s nothing worse than trying to find a specific receipt if all your receipts from that store have the exact same name. Rename files so they’re easy to find.
- While sorting things when they come in is a good idea, even the best intentions fail when we get busy. Set up a time once a week to sort anything that gets left behind.
- Don’t make a folder for every single thing. You don’t want the solution to become worse than the problem. Group up items where you can (this is another vote in favor of sorting by project).
If you need help with your businesses Microsoft 365 subscription and OneDrive, or just for tackling the topic of backups once and for all – Valley Techlogic is here for you. We even have our own backup solution for servers, TechVault. Learn more with a quick consultation today.
Looking for more to read? We suggest these other articles from our site.
-
With Windows 11 out now, how many people are still using Windows 7?
-
Windows 365 and the Pros and Cons of Virtualization in Cloud Computing
-
10 things you can do today (yes today) to make your business’s network safer
-
Unsure if the person you’re interacting with may be a fake? This Chrome extension can detect fake profile pictures with 99.29% accuracy
This article was powered by Valley Techlogic, an IT service provider in Atwater, CA. You can find more information at https://www.valleytechlogic.com/ or on Facebook at https://www.facebook.com/valleytechlogic/ . Follow us on Twitter at https://x.com/valleytechlogic.