We’re announcing this a bit late, but we did want to touch on this annual event (now in its 18th year). Every year CISA (Cybersecurity and Infrastructure Security Agency) releases new resources that are free to download and share for Cybersecurity Awareness Month. The theme this year is “See Yourself in Cyber” and we appreciate the effort to help everyone understand that cybersecurity measures are up to all of us to maintain.
So many cybersecurity measures feel very passive, you’re protected by your anti-virus or firewall automatically. Your IT team helps you navigate any issues that make come up. For businesses, advanced cybersecurity threat protection can detect a threat just from activities that fall outside the norm (like your computer being online at three in the morning) and send you a warning.
Unfortunately, hackers are always trying to circumvent these automatic measures no matter how advanced they become. The human element is still the biggest cybersecurity threat to your network and business. That’s why acknowledging we all have a role to play in preventing cyber threats is so important.
CISA recommends four important steps we all need to take online:
- Think Before You Click: Before you click on that link in an email or download an attachment, do a little research. Is the sender who you expect it to be? Phishing emails are still the #1-way users are hacked.
- Update Your Software: This is good common-sense advice; most patches also include important security updates and it doesn’t take very long to install them (and for Windows devices you can even have them run automatically).
- Use Strong Passwords: This is another easy one and if you use one of our password manager recommendations, it’s even easier to create stronger passwords that you don’t have to manually remember.
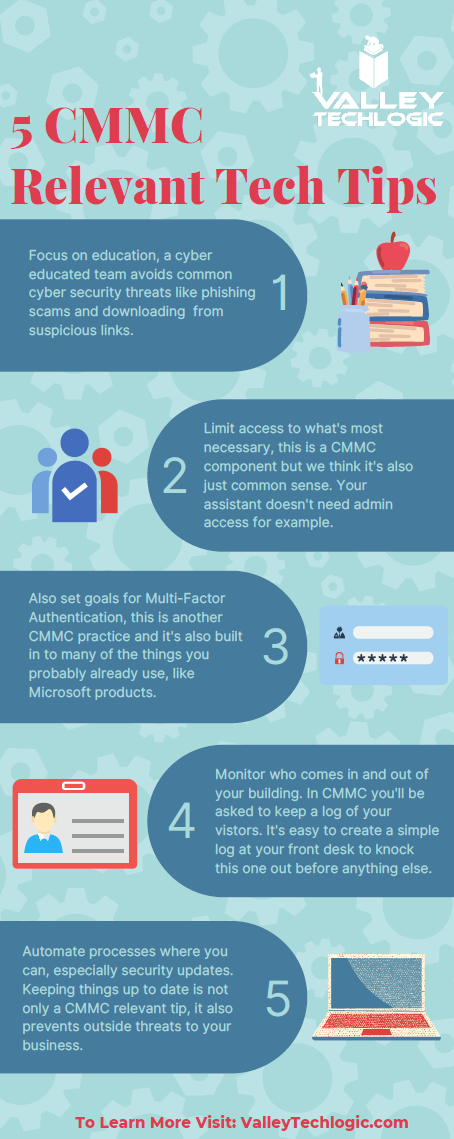
- Enable Multi-Factor Authentication: This is CISA’s fourth tip for this year and lucky for you we have a guide for this too.
These tips may seem simple, but they will be hugely beneficial to preventing a cyber threat for you, your business or your employees. However, you can take it a step further and engage with cyber security training.
You may be wondering what that would look like, well you’re in luck. We have a sample training session right here for you to review with your employees:
 This is just a quick sample lesson; through our partner we have bite sized lessons that include video that you and your team can take to beef up your cybersecurity knowledge. They average 2-3 minutes long with a quick quiz at the end to make sure the knowledge was absorbed, and you can even see your employees average scores to see how everyone is doing.
This is just a quick sample lesson; through our partner we have bite sized lessons that include video that you and your team can take to beef up your cybersecurity knowledge. They average 2-3 minutes long with a quick quiz at the end to make sure the knowledge was absorbed, and you can even see your employees average scores to see how everyone is doing.
If you incentivize taking this training it will not only be a team building opportunity, it will also help your business stay safe from cyber security threats. If you’d like to learn more about cybersecurity training or stepping up your cybersecurity measures in your business (including the aforementioned advanced cyber threat detection) reach out today for a consultation.
Looking for more to read? We suggest these other articles from our site.
-
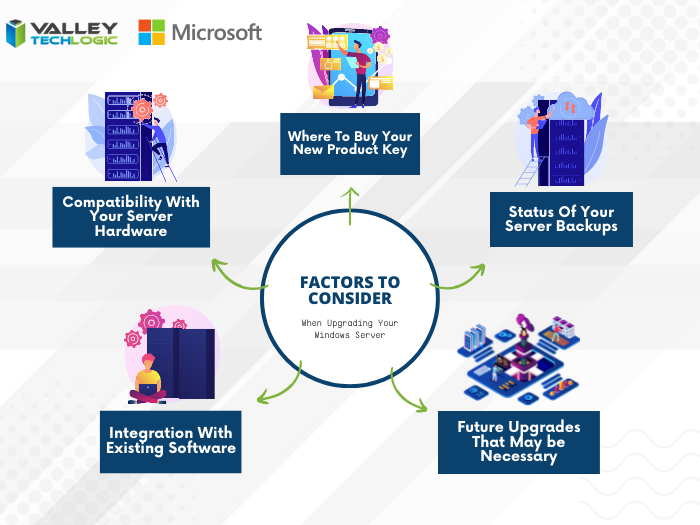
Windows Server 2012 and Server 2012 R2 are approaching end-of-life, what should you do?
-
Is it time to call in the reinforcements? 5 benefits to co-managed IT services
-
On average, your information is shared 747 times a day according to a new study
-
College shuttered after 157 years due to ransomware attack
-
When the business is you, how data brokers create and sell detailed information based on your browsing history
This article was powered by Valley Techlogic, an IT service provider in Atwater, CA. You can find more information at https://www.valleytechlogic.com/ or on Facebook at https://www.facebook.com/valleytechlogic/ . Follow us on Twitter at https://x.com/valleytechlogic.