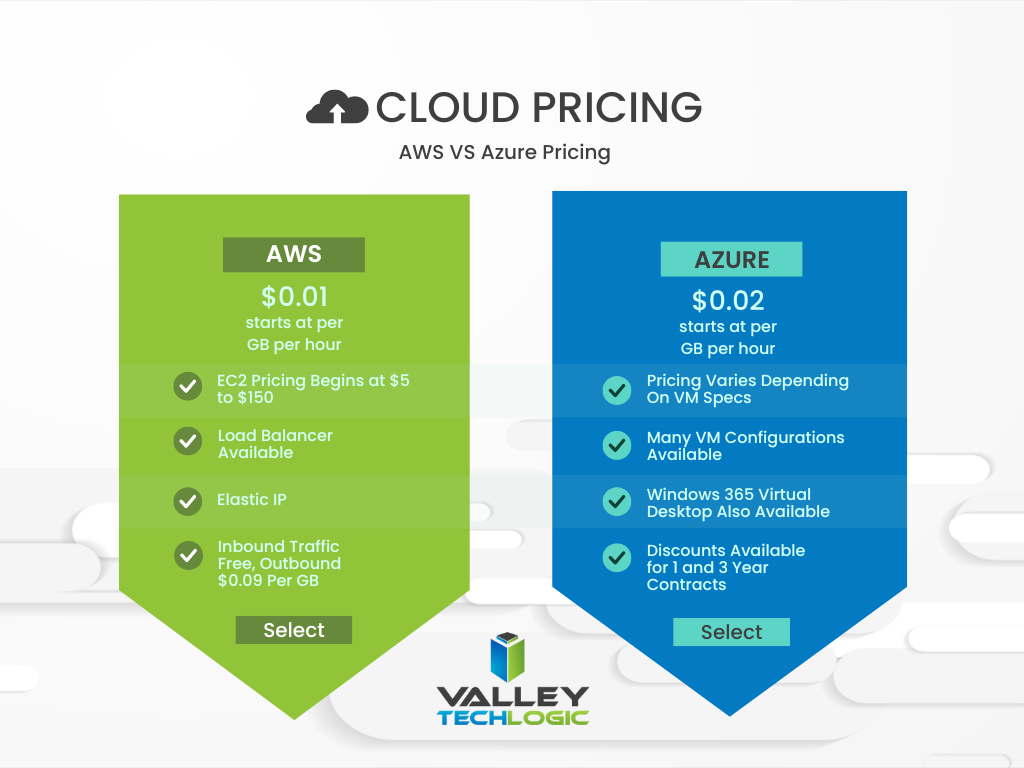
Windows Server 2012 and Windows Server 2012 R2 are quickly approaching their End-of-Life date of October 10, 2023. This is just over 2 short months away and in the world of data migration (especially as it relates to servers) that doesn’t give you a lot of time if you’re still using this operating system in your business.
If you’re not in the loop you may be wondering what the big deal is with letting it lapse, it’ll still work right? Well yes and no. The timing of this End-of-Life event coincides with when Microsoft usually does their biggest feature and security updates for the year (typically October).
This means that those still using Windows Server 2012 will miss out on these updates, and all future updates to come unless you sign up for extended support (at a cost) and even then, that will only provide you with some security updates, there will be no future feature updates for Windows Server 2012.
You may be on the fence because you aren’t sure if you want to continue using an on-premises server or make the move to the cloud. We actually wrote a detailed article on this topic before and how it relates to the pros and cons of moving to the cloud or remaining with an on-premises server. You can find that article here.
If you are planning on trying to upgrade soon, we have a couple of steps we can recommend as you prepare:
- Decide which operating system you’ll be upgrading to. Typically we recommend upgrading to the most current operating system to give you the longest span of time before an upgrade will be needed again, however depending on your hardware or even specific software you use in your business this may not be feasible. We suggest having your server evaluated to determine which upgrade makes sense (or if an upgrade is even possible.
- If you discover your server can’t be upgraded, you’ll need to make plans for a new system. If you have an older server (over 5 years) you’ll need to determine whether an upgrade to the most recent version of Windows Server is even possible. If it’s not, you’ll have to pivot to purchasing a new system instead. There are many benefits to upgrading to a new server and an IT provider like us can help you narrow down your choices based on your business’s needs.
- Decide whether a clean installation is possible. If most of the data on your server is backed up elsewhere, for example if you have duplicate copies of your data in the cloud (which we highly recommend) then you can do a clean install without having to worry about the data already on the device.
- If a clean installation is not possible, you will need to do a migration. A migration is a slower process of updating your server to the latest version. If you’ve ever upgraded the operating system on your computer, you can probably relate as it’s similar just much longer and with more potential pitfalls. We only recommend a migration be attempted by a qualified IT technician.
- Plan for the future now. Scrambling to figure out what to do when an End-of-Life event for your device is coming up is stressful and fortunately, avoidable. Modern versions of Windows Server can perform what’s called an “In-place upgrade” which means an upgrade can occur with very little downtime or stress. Staying on top of your Microsoft and Windows updates and upgrades will mean you have the most secure version of their systems available and much less chance of a catastrophic failure occurring on your devices.
To help with your planning for Microsoft’s upcoming End-of-Life events, we’ve created this chart with the latest dates to keep track of.
If you need assistance with upgrading your Windows Server 2012 or Windows Server 2012 R2 device, or have questions about Microsoft products in general, Valley Techlogic can help. We are long time Microsoft partners, and our technicians have a wealth of experience in supporting Windows devices and navigating Microsofts offerings. Schedule an appointment today to learn more.
Looking for more to read? We suggest these other articles from our site.
-
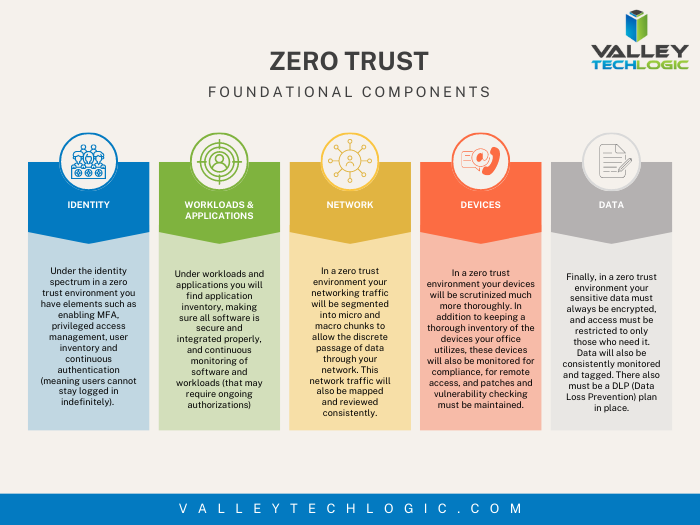
Zero trust or zero effort, how does your businesses security stack measure up?
-
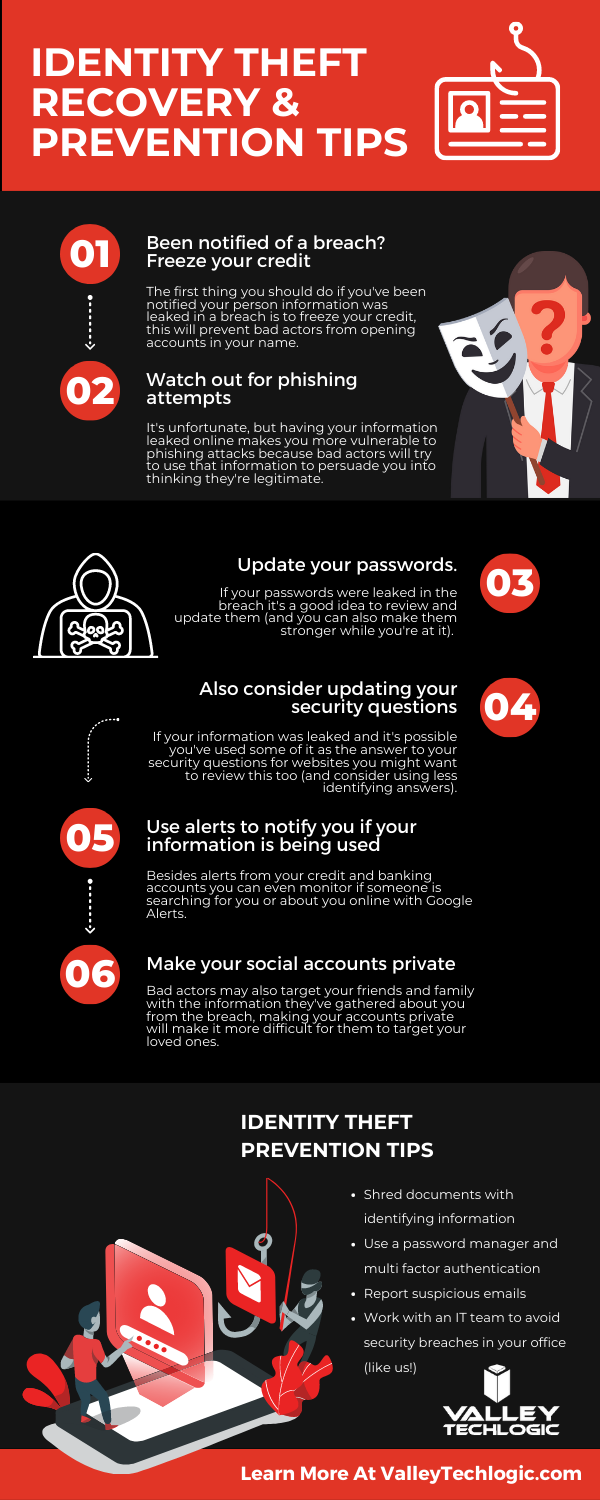
Zero-click exploits, how they work and how to avoid them
-
The US has declared a $10 million dollar bounty for more information on this ransomware
-
California retiree’s pensions possibly in limbo after data breach targets the nation’s biggest pension funds
This article was powered by Valley Techlogic, an IT service provider in Atwater, CA. You can find more information at https://www.valleytechlogic.com/ or on Facebook at https://www.facebook.com/valleytechlogic/ . Follow us on Twitter at https://x.com/valleytechlogic.