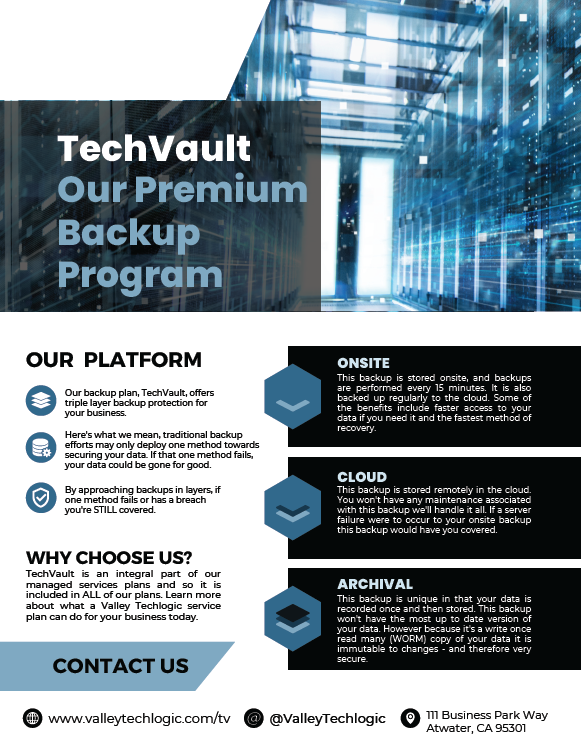
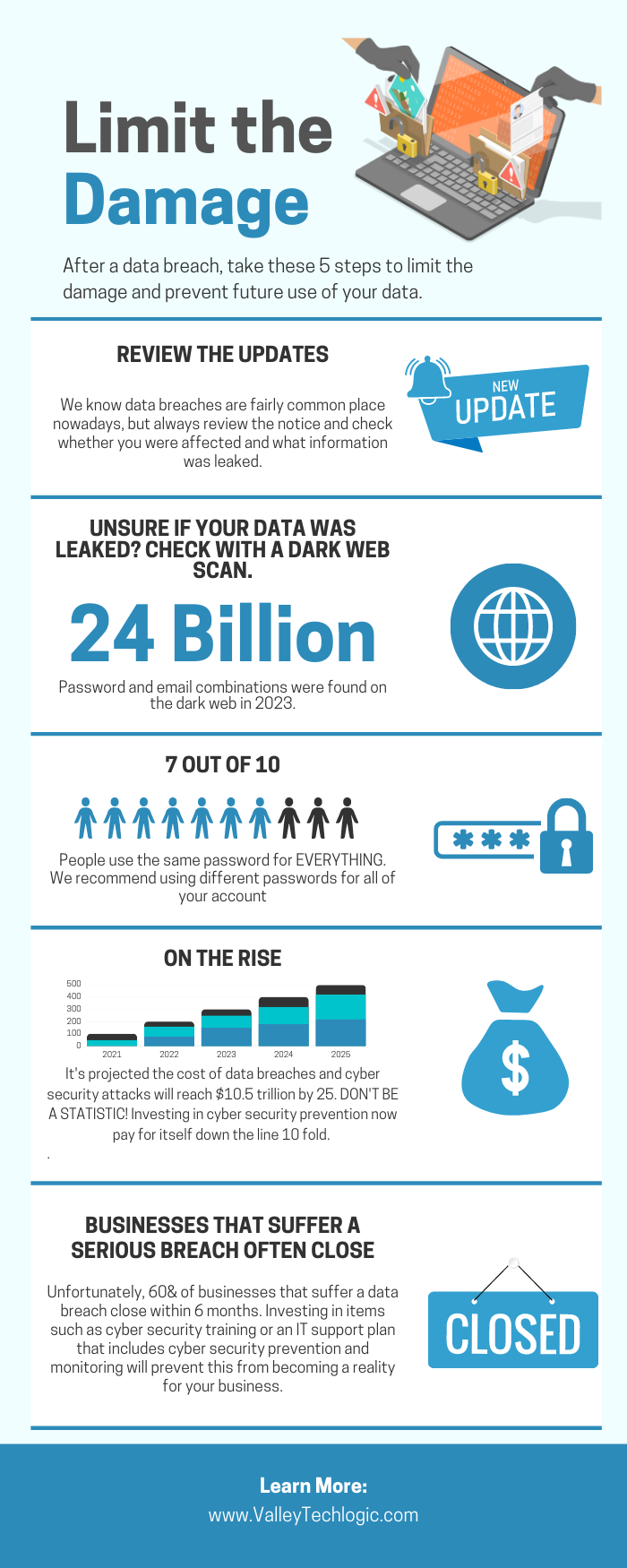
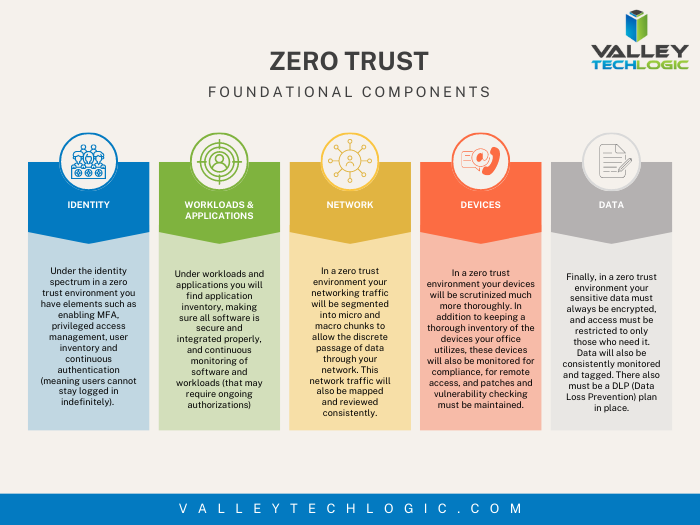
The advent of the internet brought an influx of information right to our fingertips, and unfortunately not everything that proliferates on the internet is factual.
With “fake news” undoubtedly being one of the official buzz word phrases of the 2020’s, how close are you reviewing these common place technology tropes? These are the top 10 technology myths and urban legends we see as a technology provider:
- Privacy/Incognito mode is DEFINITELY private: We’re sorry to say, if you think everything you’re doing in a private/incognito browser is hidden from view you would be incorrect. The way this mode works is it hides your browsing history from other people who may use your computer, but your ISP definitely can still see what you’re doing and depending on what’s been set up at work, possibly your IT Team/employer as well.
- Leaving your phone plugged in destroys your battery: Nope this one is also false, we’re not sure how the idea of “over charging” a battery came to be but there’s zero evidence that leaving your phone or laptop on a charger for an extended period of time will have a long-term effect on your device’s battery.
- At the same time, don’t let your device die completely before charging it: Letting a battery discharge completely before charging it again will not improve your phone’s battery life. Just charge your devices when they need a charge and let these myths about batter life go.
- Mac/Linux devices (basically anything not Windows) are virus proof: Nope again, the bad news is if a device has access to the internet, it’s going to be a target for hackers. If even your smart fridge Isn’t safe, what makes you think any computer or cellphone would be?
- Force killing apps save resources and speeds up your computer: If you have ever opened your computers task manager you’ve probably seen a lot of processes running, and you may have even force closed some of these processes to “speed” up your computer. It doesn’t really work that way unfortunately, many of the processes you see are background processes that your computer needs to run. Your computer will just open them again automatically, effectively making this activity a waste of time. You can, however, close applications you’re not using the regular way (and if you’re still having issues, it might be time to look at upgrading your device).
- Full bars mean the best service: We’ve heard it time and again, “I have four bars!” someone will exclaim, indicating that their cellphone service has reached its full potential. More bars just mean stronger signal strength, but unfortunately for you if you’re in a heavily populated urban area it means you’re sharing that same strong signal strength with everyone else in the area. Mobile service, just like any other internet service, is subject to bandwidth load so even with a strong signal you may still experience slow service depending on where you are and how many other people are around.
- You shouldn’t shut your computer down at night: This is another head scratcher for us, but we still see folks who believe they shouldn’t shut their computer down when they walk away for the evening. We’re happy to report that shutting down your computer will not harm it, in fact reducing the load on it each day by turning it off at night may even extend the life of your device.
- Magnets will wipe your data/destroy your device: There’s a little bit of truth to this one but it’s run amok for so long that the truth has been obfuscated for most folks – we’re happy to report your device will NOT be destroyed by a common refrigerator magnet. However, a really big industrial magnet could do some damage, so we suggest not placing your computer near one of those.
- Cellphones etc. can give you cancer: Nope, this one has been completely debunked. The radiofrequency that is emitted by your cellphone, tablet, laptop etc will NOT give you cancer.
- I’m a small business/single person, no hacker will bother with me: This is unfortunately, quite untrue. It’s estimated half a million U.S. accounts are hacked each day – many of these are just regular folks or small business owners like yourself.
We hope this article helped in quashing some of these myths for you but if you have any other technical urban legends you’re not sure about, we’d be happy to weigh in (just jump on our live chat and ask away!).
If the last one was a scary one for you and you’re a business owner in California, Valley Techlogic can assist. We provide cyber security services for our clients that make sure they won’t be part of that frightening statistic. Learn more through a consultation today.
 Looking for more to read? We suggest these other articles from our site.
Looking for more to read? We suggest these other articles from our site.
-
Maximizing your tax deduction potential with Section 179
-
Threat actors attack on cloud company leads to customers data being wiped completely
-
Looking to up your online platform game? These 5 tools will help you run your online business better
-
Discord.io data breach sees 760,000 users information stolen and an end to the service
This article was powered by Valley Techlogic, an IT service provider in Atwater, CA. You can find more information at https://www.valleytechlogic.com/ or on Facebook at https://www.facebook.com/valleytechlogic/ . Follow us on Twitter at https://x.com/valleytechlogic.